165.1厘米。 5'5指的是5英尺5英寸,换算成英寸为: 5'5 = 5 x 12 + 5 = 65 1 = 2.54厘米 所以 5'5 = 65 x 2.54厘米/in = 165.1厘米。 英寸(吋)是使用于联合王国 (uk,即英国 (英联邦)及其前殖民地的. Dj osmo action 5 pro 拥有最佳防水性能,并配有内置气压计,不过也有水下保护壳可供选择,以进一步提高专业潜水员的防水性能,gopro 提供可选的 60 米防水水下保护壳。 dj osmo. 5的倍数的个位数字非0即5。 奇数 ade曲线一共有5类。 有理二重点一共有5类。 伽罗华理论:5次方程不再有求解公式,小于5次的方程却都有求解公式。 著名的矩阵博士在计算机出现之前就预言,π的.
27 Biggest Data Breaches Globally (+ Lessons) 2025 Huntress
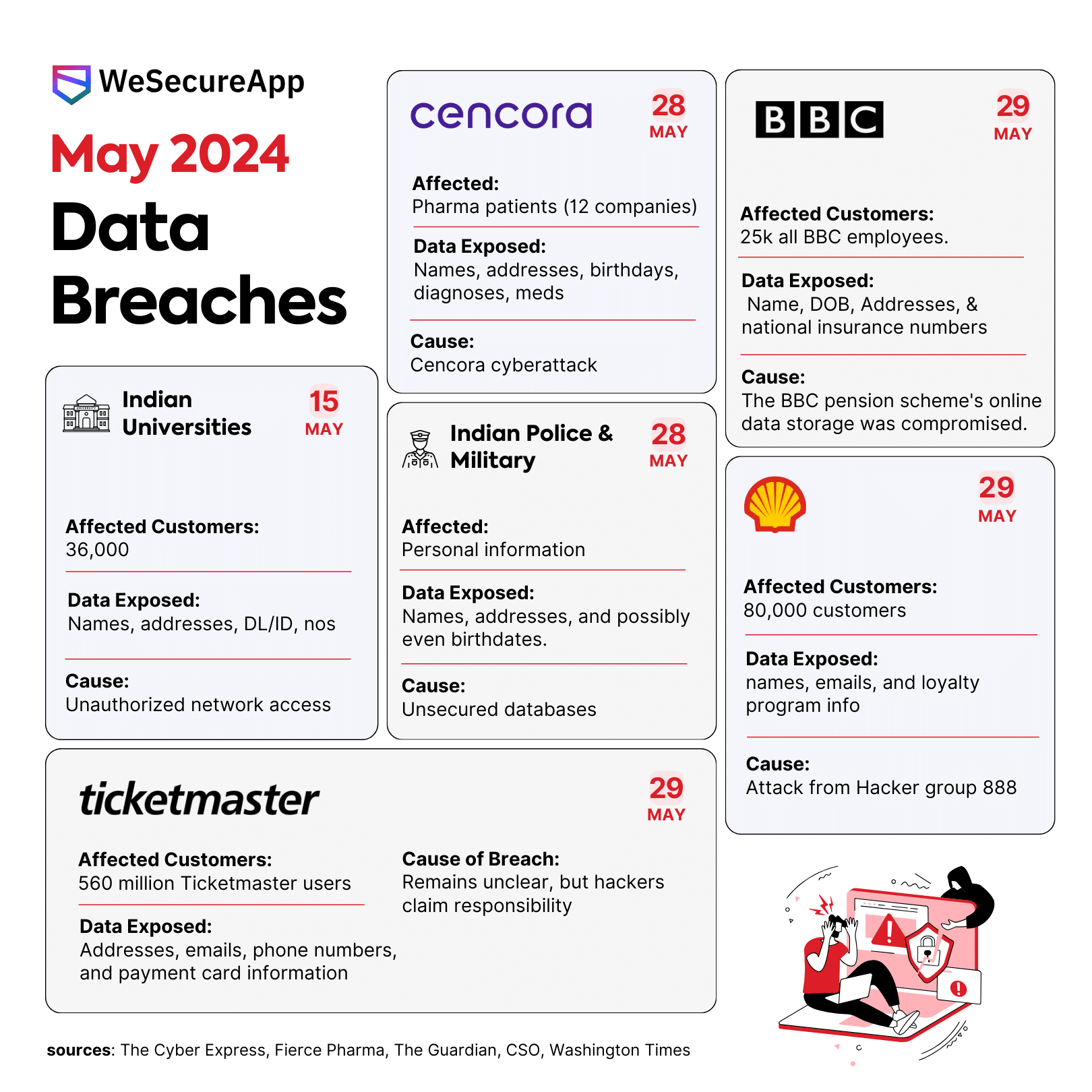 Understanding The Marietemara Data Breach ICRW — Creator Insight Briefs
Understanding The Marietemara Data Breach ICRW — Creator Insight Briefs
Details
 Understanding The Marietemara Data Breach ICRW — Creator Insight Briefs
Understanding The Marietemara Data Breach ICRW — Creator Insight Briefs
Details
 Explore What is Data Breach and How to Prevent It Gcore
Explore What is Data Breach and How to Prevent It Gcore
Details
![110+ of the Latest Data Breach Statistics [Updated 2025]](https://i2.wp.com/secureframe.com/_next/image?url=https:%2F%2Fimages.prismic.io%2Fsecureframe-com%2FZfkakQ4qyfNhFxiZ_BiggestDataBreaches2023.png%3Fauto%3Dformat%2Ccompress&w=1920&q=75) 110+ of the Latest Data Breach Statistics [Updated 2025]
110+ of the Latest Data Breach Statistics [Updated 2025]
Details
 The Changing World of Data Breaches with Troy Hunt Easy Prey Podcast
The Changing World of Data Breaches with Troy Hunt Easy Prey Podcast
Details
 Life Changing Data Breaches Got a Backup Plan? Medium
Life Changing Data Breaches Got a Backup Plan? Medium
Details
 Types of data breach attacks. Types of data breach attacks. Download
Types of data breach attacks. Types of data breach attacks. Download
Details
 27 Biggest Data Breaches Globally (+ Lessons) 2025 Huntress
27 Biggest Data Breaches Globally (+ Lessons) 2025 Huntress
Details
 7 Most Common Types of Data Breaches That Can Affect Your Business
7 Most Common Types of Data Breaches That Can Affect Your Business
Details
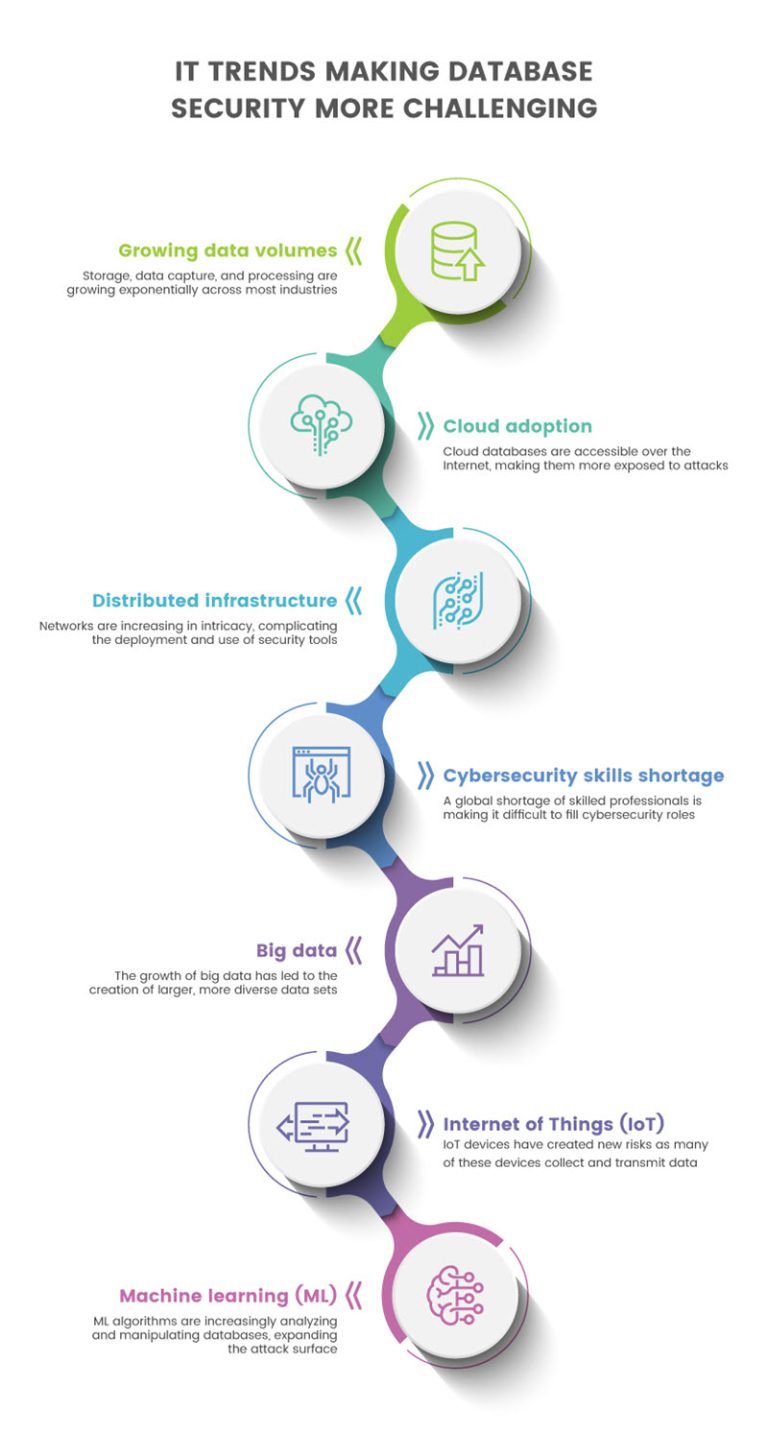 What is Database Security Threats and Best Practices}
What is Database Security Threats and Best Practices}
Details



![110+ of the Latest Data Breach Statistics [Updated 2025]](https://i2.wp.com/secureframe.com/_next/image?url=https:%2F%2Fimages.prismic.io%2Fsecureframe-com%2FZfkakQ4qyfNhFxiZ_BiggestDataBreaches2023.png%3Fauto%3Dformat%2Ccompress&w=1920&q=75)





