绝对不可能。 老文明玩家都知道一个逻辑,那就是 文明系列,单数代必然比双数代写实。 所以除非 席德梅尔 疯了,否则7代应该是像五代那样回归写实,而不是继续走趣味路线。 只要是先接触3代再玩4. I7 14650hx 和ultra 7 255hx这两款cpu的发布时间不同,两款cpu的发布时间整整相差一年,已发布版本也是相差2个版本,中间还有个ultra 一代(貌似没有推出hx处理器)。这两个cpu在ai能力上有很. 在《文明7》中再来一回合! 今年slg开年最大的新闻大概就是文明7 首发了,作为时隔十年的正式作品,文明7在部分媒体评分爆表,但玩家并不买账。 为什么会形成这样的情况呢? 文明7没做创新吗?
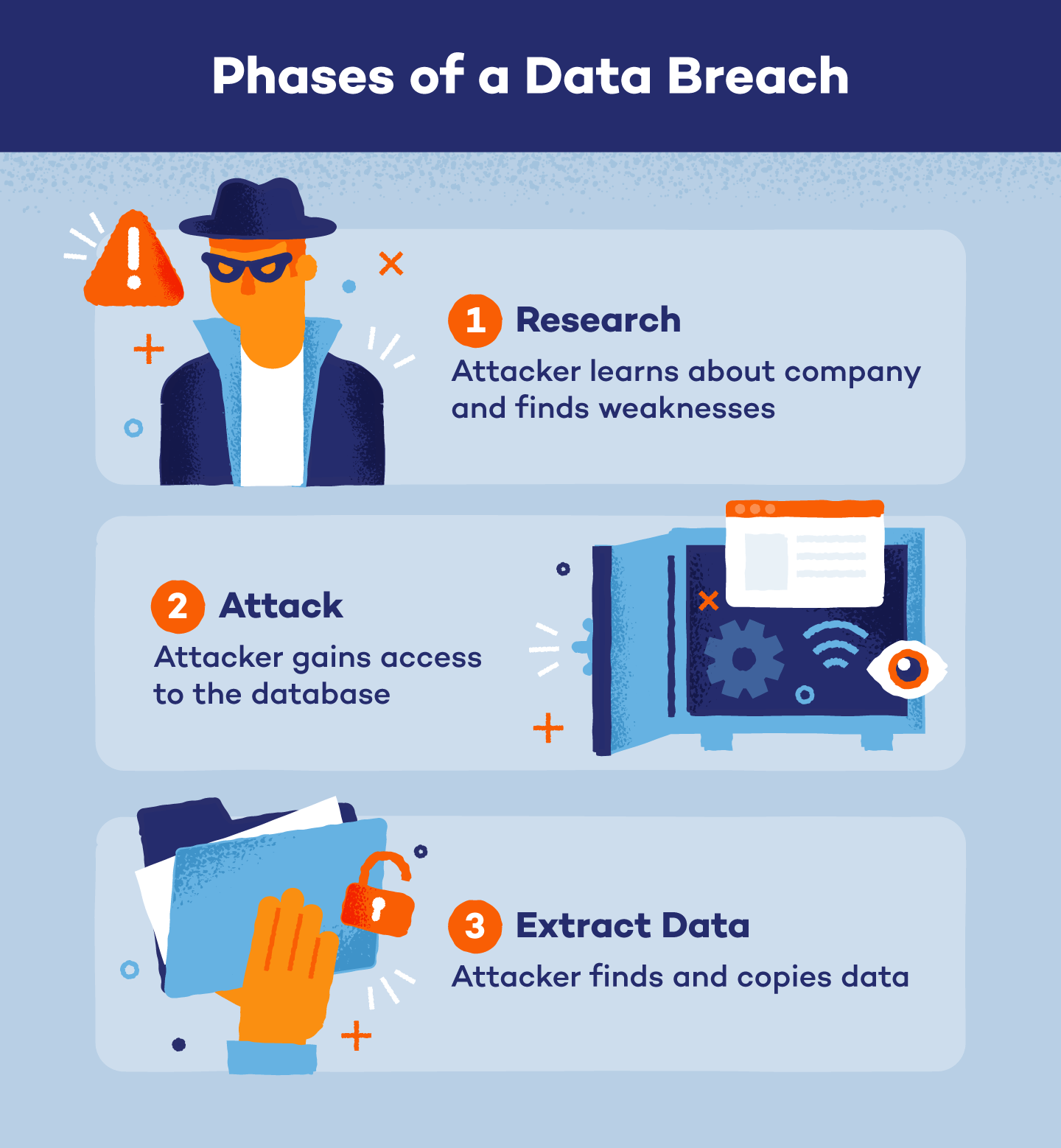
How Does a Data Breach Occur? and How to Recognize a Data Breach