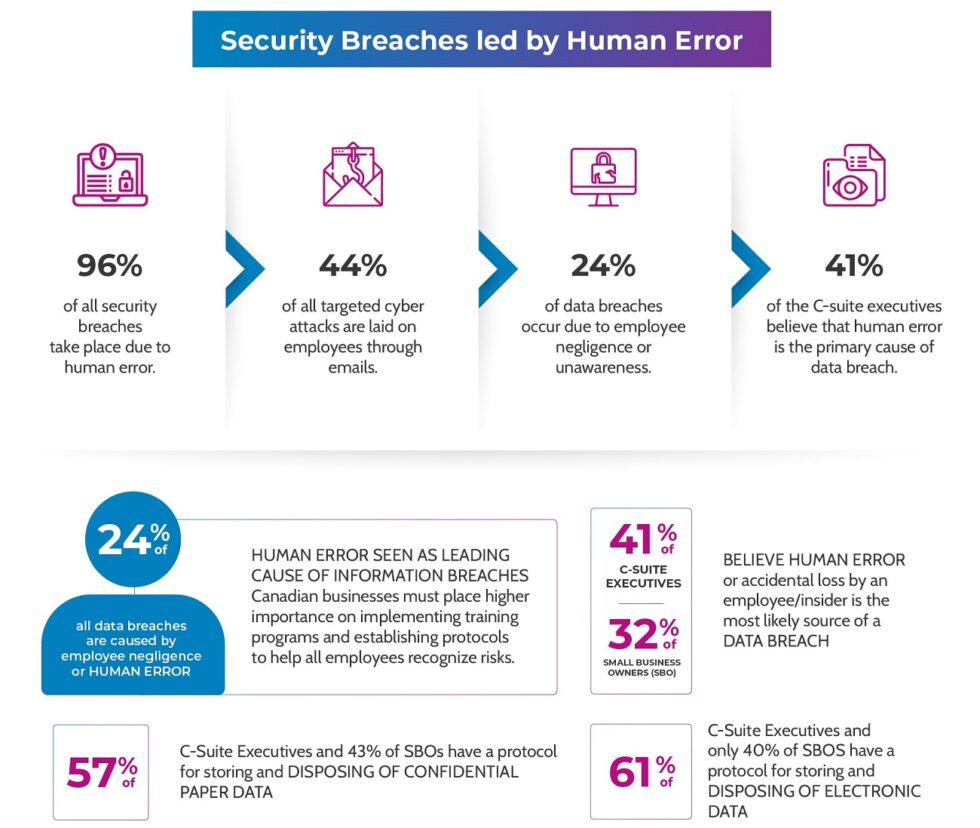
Insecure by design The hidden risks that can lead to a data breach








常山消失 三国历史中的赵子龙 (公元154—229年),就出生在东汉末年常山国真定县,故逢人必称自己乃“常山赵子龙”是也。 唐朝宝应元年 (约公元762年)后常山郡改成“恒州郡”.









