Explore all the ways youtube is empowering creators and making our platform the best place to create, period. Get the official youtube app on iphones and ipads. Get the official youtube app on android phones and tablets.
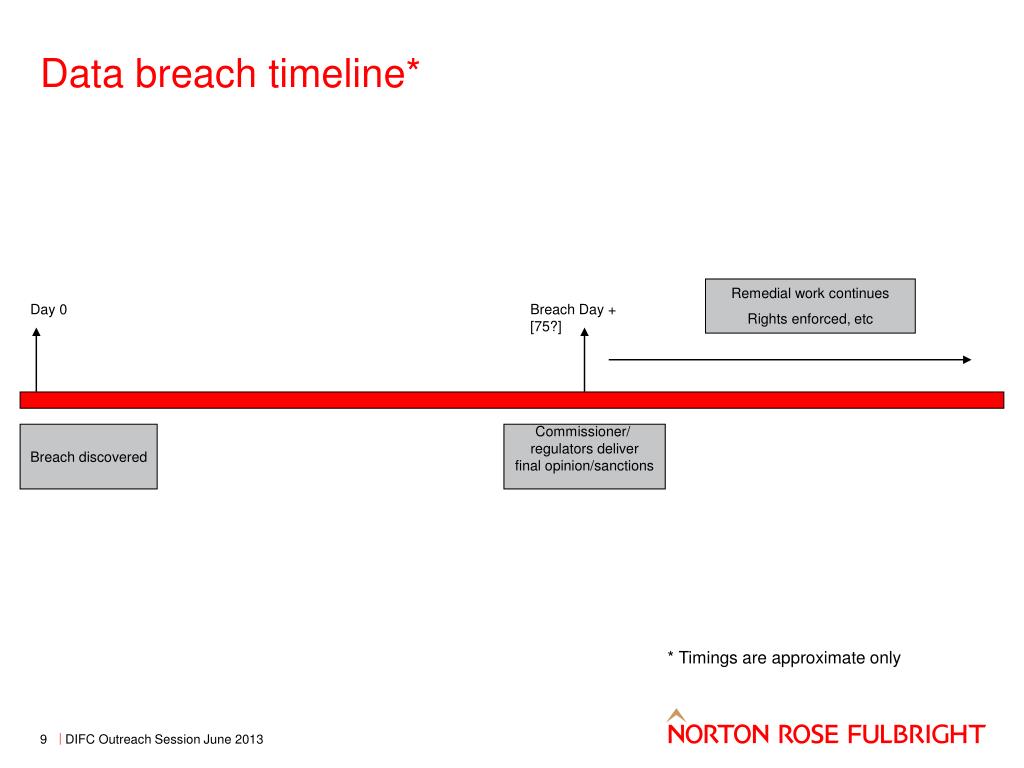
72 Hours Understanding the GDPR Data Breach Reporting Timeline
Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on youtube.
![Top Known Data Breaches of 2022 [Timeline + Infographic] Venngage](https://i2.wp.com/venngage-wordpress.s3.amazonaws.com/uploads/2022/09/Data-Breach-2022-Timeline-Template-preview-730x2281.png)



![Top Known Data Breaches of 2022 [Timeline + Infographic] Venngage](https://i2.wp.com/venngage-wordpress.s3.amazonaws.com/uploads/2022/09/Data_Breach_2022_Blog_Header.png)