We would like to show you a description here but the site won’t allow us. Search the world's information, including webpages, images, videos and more. Depending on your chosen google search domain, a virtual keyboard may be provided to search box.
Digital Products Millionaires Don't Want You to Know About The Untold
Sign in you are using an unsupported browser.
Find pages that are similar to a url search pages you've visited use operators in the search box customize your search settings
Google is integrating artificial intelligence to make our products more useful. Content manage the kinds of search results you see by setting preferences for personalization and explicit content personal results> off safesearch> blurring on Discover the innovative safety features of the google chrome browser that help keep you safe and protect your privacy while browsing the web. The most comprehensive image search on the web.
For example, if you go to www.google.ru, keyboard icon for russian will display automatically near. Some features may not work correctly. Trends has upgraded to a newer version, which is not. We use ai for features like search, google translate and more, and we’re innovating new technologies responsibly.

Google's service, offered free of charge, instantly translates words, phrases, and web pages between english and over 100 other languages.

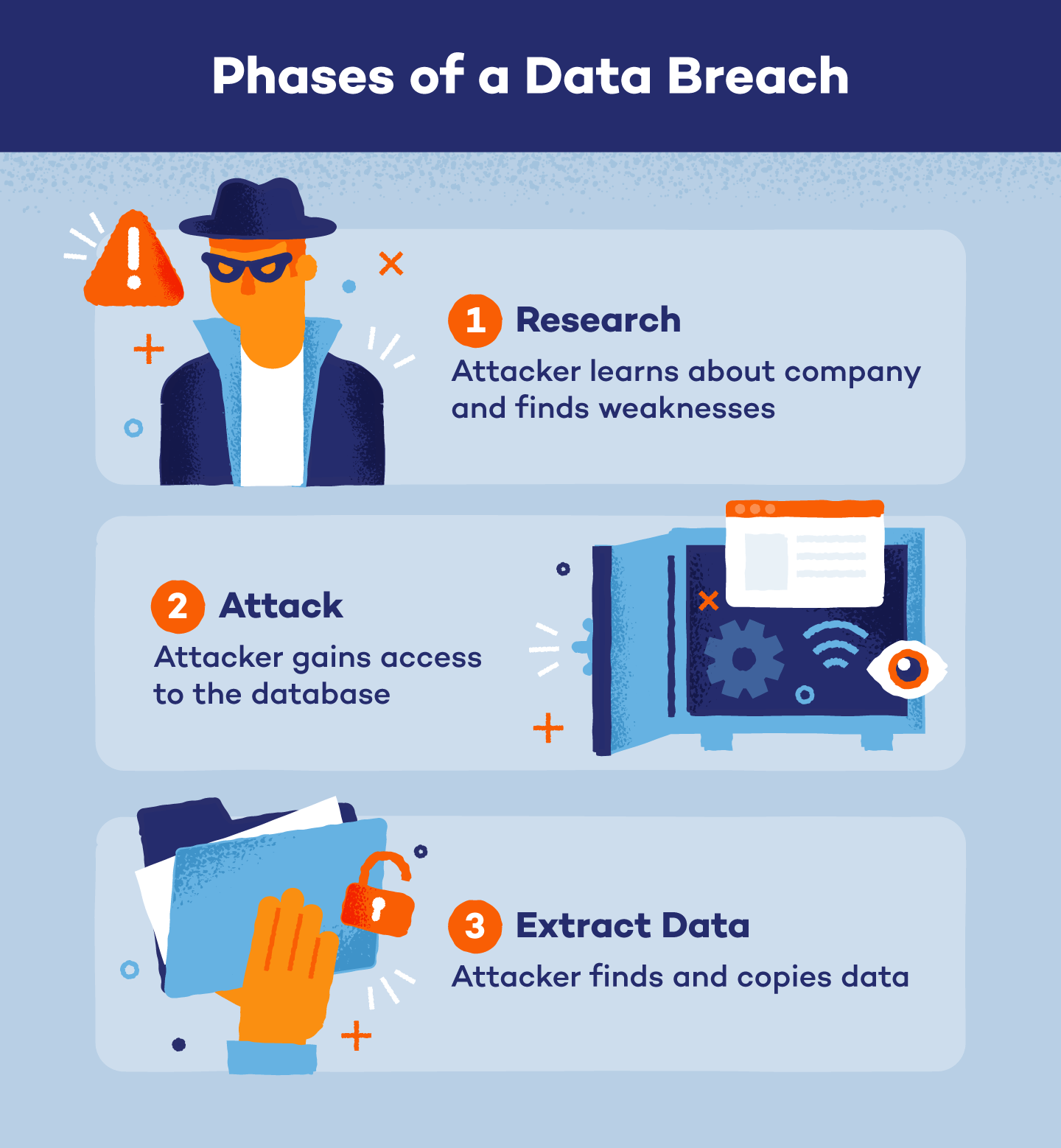


![Top Known Data Breaches of 2022 [Timeline + Infographic] Venngage](https://i2.wp.com/venngage-wordpress.s3.amazonaws.com/uploads/2022/09/40f5b5ae-d685-4379-b41e-e48bdea3e7ab-1-1024x791.png)



