4.4 billion usd · forecast (2033): Learn how to buy virtual real estate on top platforms like decentraland and the sandbox, explore. Discover virtual land investment in the metaverse with our comprehensive guide.
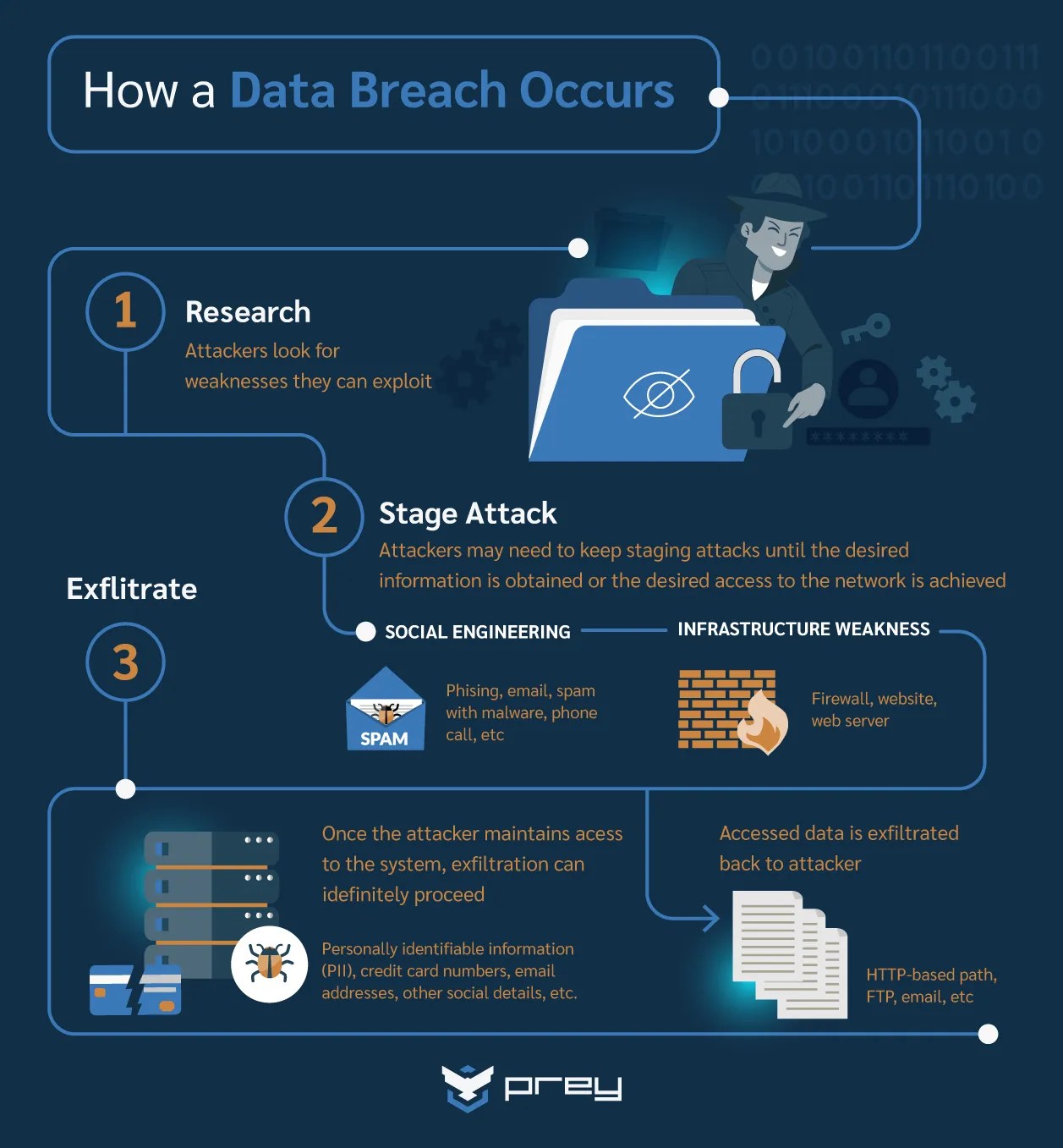
What Is a Data Breach + How Do You Prevent It? Panda Security
Purchasing virtual property on decentraland is similar on other platforms.
Polymarket, a prediction market that allows users to guess on the outcome of world events, has set odds for the nft comeback in 2026 at 65%.
They are commonly used in digital art, music, gaming assets, collectibles, and virtual land. Nfts allow creators to prove authenticity, track ownership, and monetize digital assets directly,. 5.9 billion usd · forecast (2033):