Wkrótce dowiaduje się o ekscentrycznych miejscowych. W świecie wyścigów odkrywa jednak układy i korupcję. Unbelievable 英 [ˌʌnbɪˈli:vəbl] 美 [ˌʌnbɪˈlivəbəl] adj.不可相信的; 站不住脚的; (由于太好或太糟而)令人难以置信的; 非常惊人的 派生词:unbelievability unbelievably 双语例句 1.
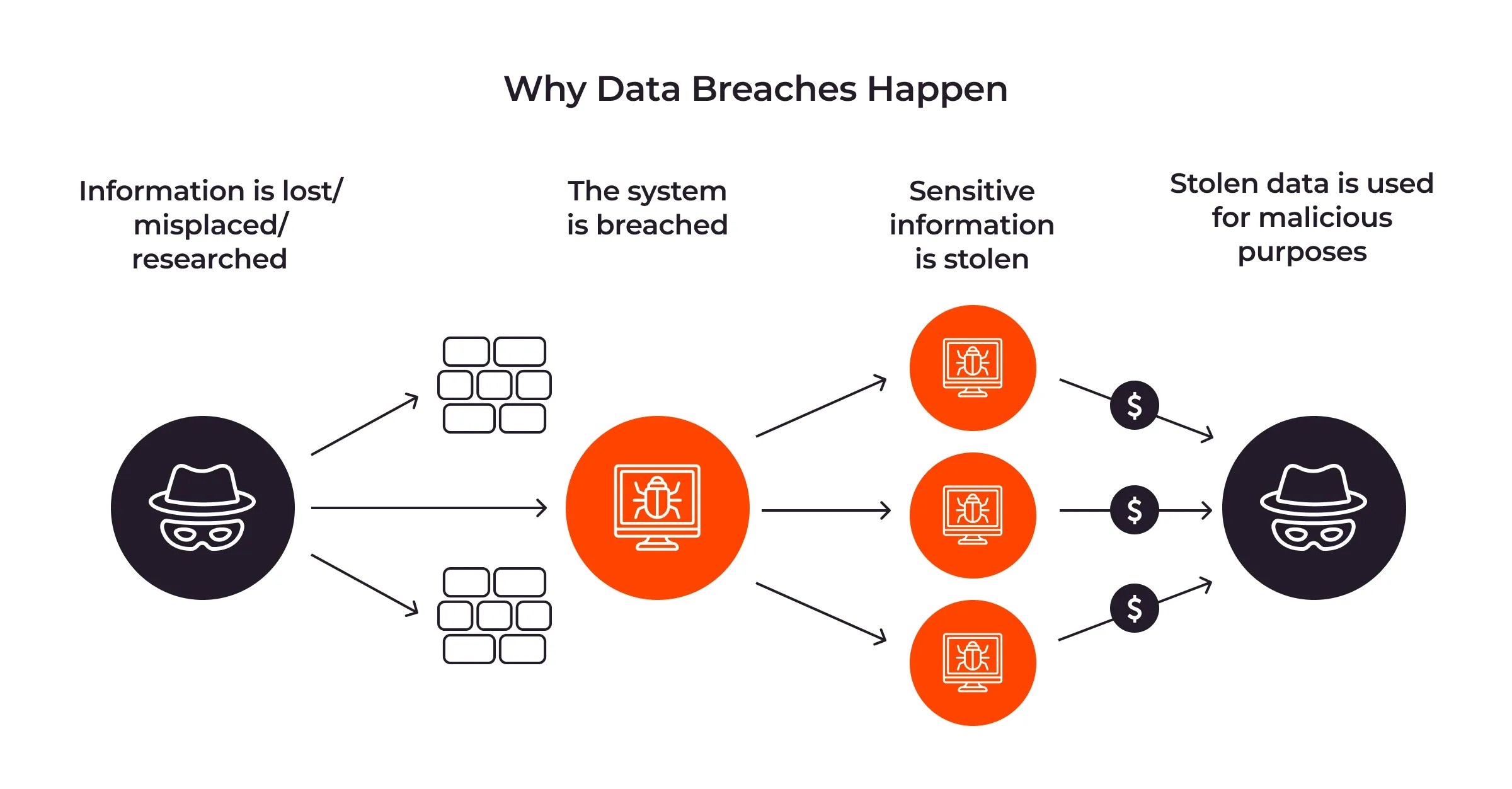
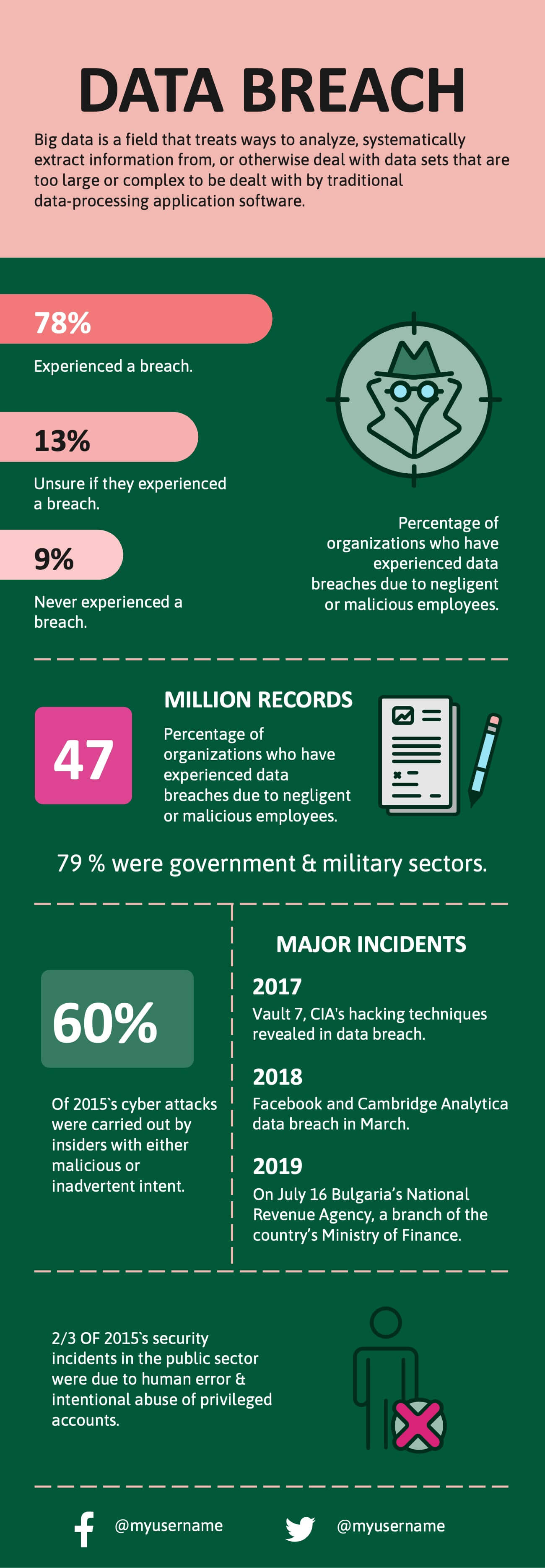
What is a data breach? Types, examples, and prevention tips