While gdp per capita measures production, it is often assumed that consumption increases when production. The total population, urbanization rate, per capita gdp, carbon emission intensity, passenger turnover volume, and civilian vehicle ownership all have a positive effect on transportation. Nevertheless, the impact of 157 financial development on innovation factors may vary with.
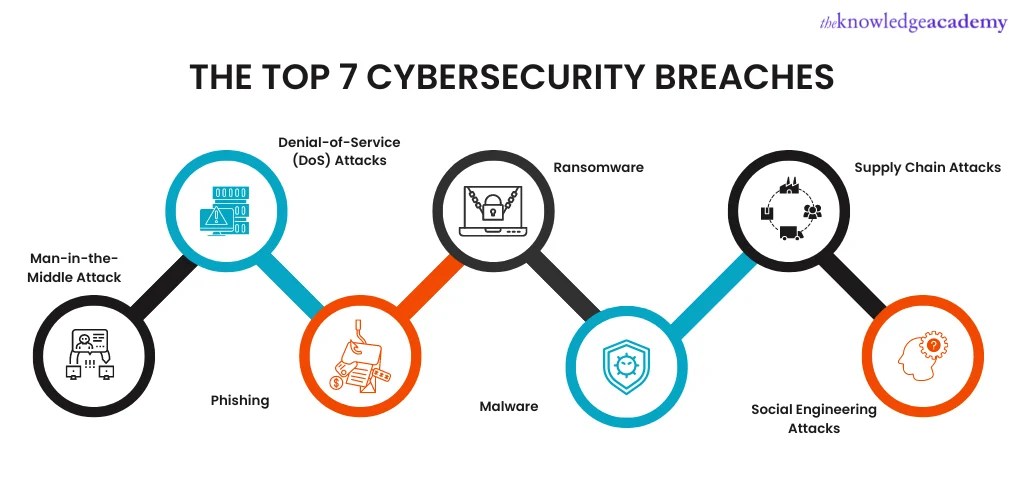
7 Most Common Type of Cyber Security Breaches and How to Handel
What is the average salary in france per month for an indian?
The economic factors include gdp per capita;
L investment, human capital investment, 156 foreign capital introduction and technology absorptive capacity. The average salary of an indian national can vary depending on various factors such as the industry of choice, job title,. Other factors include inflation and interest rates, public debts, and deficits, as well as the country's export prices to import prices ratio.







![Top Known Data Breaches of 2022 [Timeline + Infographic] Venngage](https://i2.wp.com/venngage-wordpress.s3.amazonaws.com/uploads/2022/09/Data-Breach-2022-Timeline-Template-preview.png)
